As the faces of the internet continue to evolve, information security has become a critical element of doing business. This is particularly the case of Operational Technology (OT) systems, used to manage industrial processes.
As more of these systems become interlinked and connected directly to IT Systems the importance of having proper security measures in place has never been higher. Understanding the different regulatory requirements associated with protecting OT systems from cyber threats is paramount.
Understanding OT Cybersecurity
OT refers to the technology that has the capability of identifying or inducing changes to physical devices, processes, and events within an enterprise through direct monitoring and control. While Information Technology (IT) is associated with data, Operational Technology revolves around the functioning of an organization. OT systems are extensively used in industries such as manufacturing, energy, utilities, and transportation.
The integration of OT and IT has both practical advantages and risks that have to be considered. OT cyber threats can lead to severe consequences, including physical harm, safety risks, and substantial financial losses. Hence, there is a need to ensure that OT cybersecurity is well implemented and maintained.
Regulatory Landscape
The legal requirements governing the cybersecurity of operational technologies are complex and dynamic. There are guidelines and standards that have been put in place by various international bodies or organizations, governments, and industries to protect and secure the OT systems. It is crucial to comprehend these regulations to ensure that the operations of an organization do not run afoul of legal requirements.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a well-known structured tool intended to guide the management of cybersecurity risk within organizations. The framework is based on five core functions: IDPDRR stands for Identify, Protect, Detect, Respond, and Recover. These functions offer a strategic perspective of the life cycle, through which an organization manages cybersecurity risk.
Despite being inherently developed for IT systems, the NIST framework can be applied to OT cybersecurity. As such, the framework focuses on risk management and utilizes the guidelines to suggest how organizations can improve OT security.
IEC 62443
The IEC 62443 is a set of standards developed for the industrial automation and control system (IACS). These standards offer an integrated approach to cybersecurity issues at both technical and organizational levels.
IEC 62443 has multiple parts that deal with various issues within OT security, such as security policies, system requirements, and components. By adopting such standards, it will be easier for an organization to set the right security measures that will make its OT systems ready to face any cyber threats.
NERC CIP
The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards are the mandatory cybersecurity rules that control entities in the North American bulk electric system. These standards seek to safeguard critical infrastructure from cyber risks that can impede electricity supply.
There are different elements of the NERC CIP standards that focus on personnel training for cybersecurity, the handling of cybersecurity incidents, and planning for restoration from cybersecurity incidents. Organizations in the energy sector should therefore meet NERC CIP standards to comply with industry regulations.
GDPR and Data Protection
Even though GDPR mainly deals with personal data protection, it becomes relevant to OT systems under certain conditions, especially when these systems process personal data. GDPR specifically mandates that reasonable measures must be put in place to safeguard personal data, which may involve the protection of OT systems in some scenarios.
It is crucial for organizations to address GDPR compliance and OT cybersecurity processes in sectors where OT systems manage personal data. Consequently, non-compliance leads to severe penalties and impaired organizational reputation.
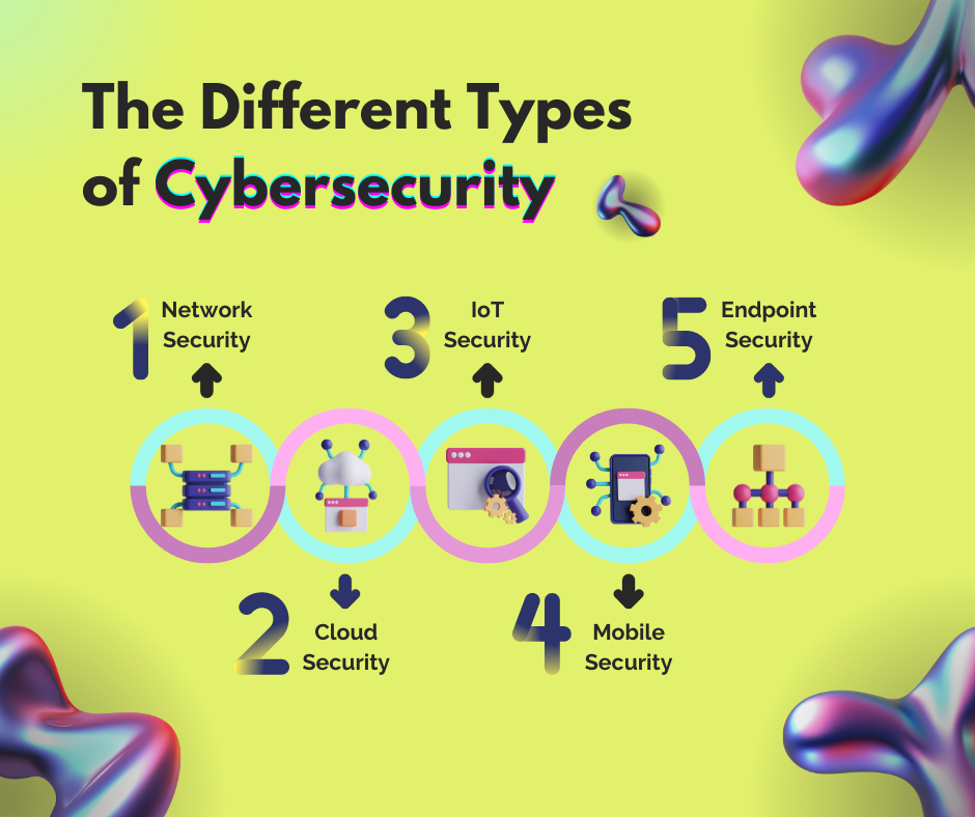
Issues in OT Cybersecurity Compliance
There are several challenges inherent in defining regulatory standards in OT cybersecurity. The compliance function is crucial in any organization, but it should be noted that organizations also require efficiency and safety, especially when it comes to operations.
Integration with Legacy Systems
A number of OT systems are outdated and were not created with cybersecurity as a priority. Implementing contemporary cybersecurity measures along with these older systems can be challenging and expensive. This means that the organizations have to look for ways of protecting these systems keeping in mind that they are used in the organization’s operations.
Real-Time Requirements
A majority of OT systems function in mission-critical scenarios where delays or interruptions have severe consequences. The main difficulty is the integration of cybersecurity measures that do not affect the response time of these systems.
Limited Resources
Companies especially the small ones may not have sufficient capital or personnel capable of implementing and sustaining robust OT cybersecurity measures. This may make it challenging to meet the regulatory requirements of any standards.
Evolving Threat Landscape
Cybersecurity threats are very dynamic as threats keep on being invented from time to time. It also implies that organizations need to be constantly informed on emerging threats and have adequate security strategies to help address these threats.
Approaches to OT Cybersecurity Standards
Despite the challenges, there are several best practices organizations can follow to navigate OT cybersecurity standards effectively:
Conduct Regular Risk Assessments
Risk management should be performed systematically to determine potential risks and the probable consequences of cyber threats on OT systems. Such evaluations should be holistic and should cover the technical and organizational aspects.
Implement Layered Security
A defense-in-depth security system can be defined as the use of multiple security layers to protect an organization’s OT system. These measures may involve network zoning, firewalls, intrusion detection systems, as well as endpoint protection.
Event Detection and Incident Handling
In this context, 24/7 monitoring of OT systems is crucial to identify and counteract cyber threats in their operational environment. Managers should ensure that effective incident response frameworks that help contain the incidents and reduce their impact are developed and implemented in organizations.
Training and Awareness
Education and sensitization are also important measures as they help employees grasp the essence of protecting OT from cybersecurity threats and their responsibilities. Periodic instruction may make the employees aware of risks that are likely to happen and maintain good security practices.
Collaborate with Industry Partners
Suppliers, customers, and regulation authorities are the primary stakeholders with whom organizations can engage in order to ensure that they are aware of the latest trends and practices in cybersecurity. Knowledge management fosters improved security and compliance in educational endeavors.
FAQs
How does IT cybersecurity differ from OT cybersecurity?
IT cybersecurity aims at safeguarding information and digital assets against cyber risks, while OT cybersecurity targets protecting the physical systems and processes that manage industrial processes. Even though both have their roots in similar areas, OT cybersecurity must consider various issues associated with real-time operation and security.
What strategies can organizations use to maintain compliance with several OT cybersecurity standards?
The case is that organizations can follow several OT cybersecurity standards by using the risk management approach and integrating a wide-ranging cybersecurity model. The possible strategies for addressing regulatory compliance issues are routine audits, constant monitoring, and cooperation with the stakeholders.
What role does constant surveillance play in OT cybersecurity?
This means that the process of monitoring needs to be ongoing since new threats are constantly surfacing and evolving. OT systems run in high-risk settings, where a delay or interruption can lead to adverse effects. The constant monitoring assists in minimizing the occurrence, detection, and impact of security breaches for the safeguarding of OT systems.
Conclusion
Understanding and meeting the existing regulatory requirements concerning OT cybersecurity is one of the critical challenges that organizations in industrial markets face. This paper sheds light on the essential standards and the measures that can be taken to improve the security of OT systems. Thus, it is vital to remain knowledgeable and take necessary precautions to protect critical operations from OT cyber threats and fulfill industry regulations.
Lynn Martelli is an editor at Readability. She received her MFA in Creative Writing from Antioch University and has worked as an editor for over 10 years. Lynn has edited a wide variety of books, including fiction, non-fiction, memoirs, and more. In her free time, Lynn enjoys reading, writing, and spending time with her family and friends.