Modern cybersecurity strategies rely on a multi-layered approach to effectively counter cyber threats. Among the tools that should be part of this security framework is a malware sandbox. By offering an isolated environment for analyzing suspicious files and links, it helps in understanding their behavior. Let’s explore the primary use cases of a malware sandbox.
Threat Analysis and Detection
The key use case of a malware sandbox is threat analysis and detection. Cloud-based services like ANY.RUN allow users to upload suspicious files or URLs into a Windows or Linux virtual machine and quickly see if they pose a threat.
Here is a sandbox analysis session of an Agent Tesla malware executable.
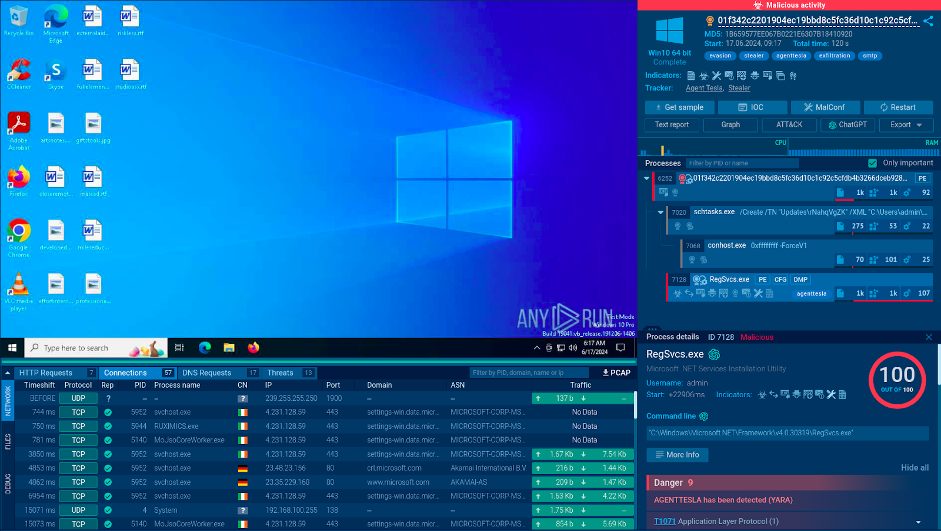
Example of a malicious file analysis in ANY.RUN
The service quickly detects the specific threat found in the file or link and provides indicators of compromise (IOCs), crucial forensic data that can be used to improve threat detection capabilities of the user’s security systems.
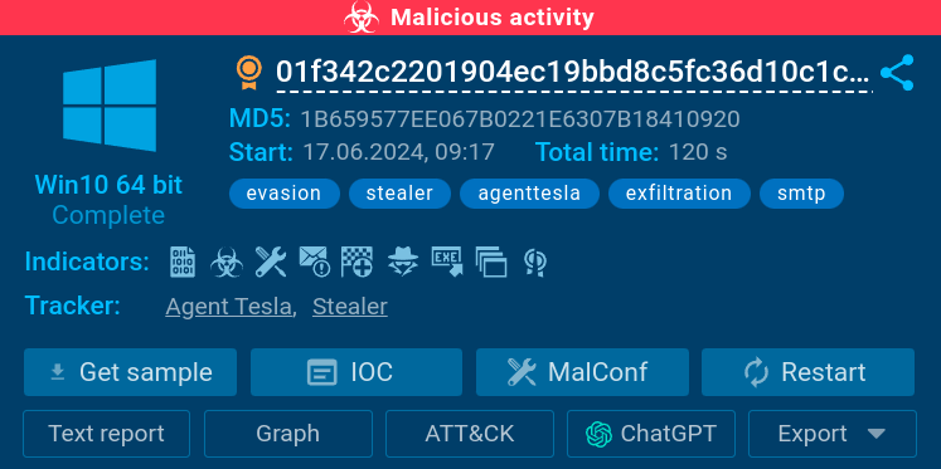
The sandbox identifies the analyzed file as the Agent Tesla malware
ANY.RUN detects threats in less than 40 seconds, providing the user with a conclusive verdict on the file or link’s threat level.
| Sign up for a free ANY.RUN account to analyze malware with no limit! |
Safe Execution and Interaction with Unknown Files and Links
For in-depth analysis of threats, it is often necessary to interact with the malicious files. Yet, doing so in a live, production environment can expose the system to significant risk. This is where a malware sandbox proves invaluable.
A malware sandbox like ANY.RUN not only provides an isolated, virtual environment, but also offers full control over it to the user. This allows security professionals to engage with the system, as well as files and links they submit for analysis to expose their behavior to the tiniest detail.
Consider the following sandbox analysis session. It lets us observe the entire process of a multi-stage phishing attack.
1. The user first uploads the phishing email to the sandbox.
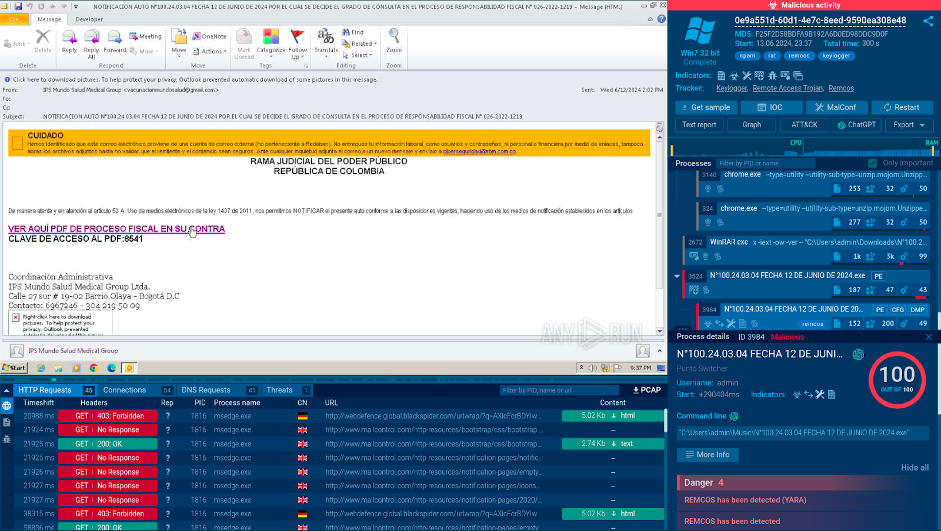
The phishing email inside the ANY.RUN sandbox
2. Inside the sandbox, they click a link found in the email.
3. The link leads to a page hosting a password-protected archive (a common technique used in malware attacks to evade detection by antivirus software).
4. The user downloads the archive and opens it by entering the password provided in the phishing email.
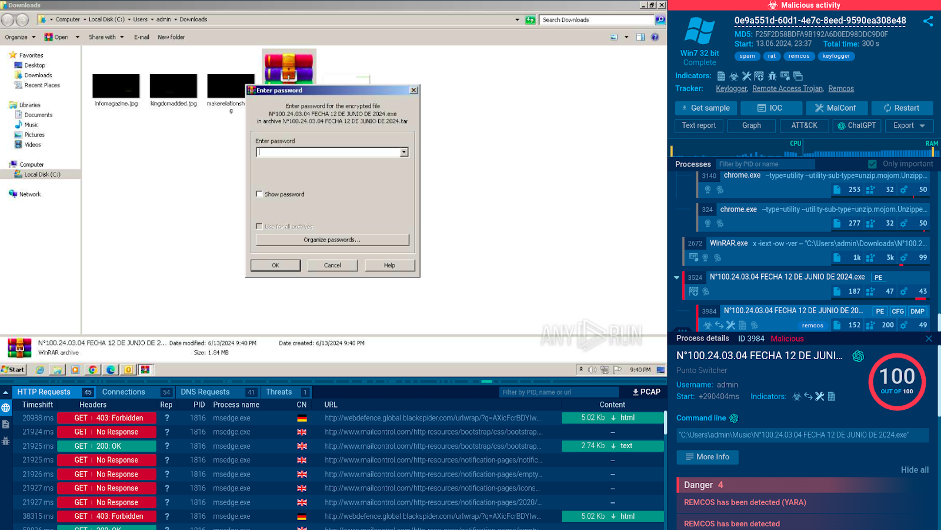
Thanks to ANY.RUN’s interactivity, users can manually enter passwords.
5. This lets the user access an executable file inside the archive.
6. After launching the executable, the sandbox instantly identifies it as the Remcos malware, a known remote access trojan.
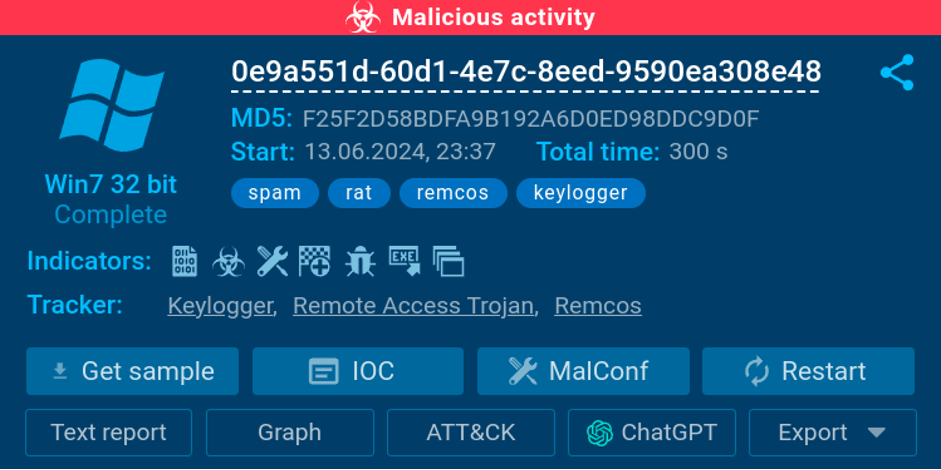
The malicious attachment is identified as Remcos
Understanding Threat Activity
Understanding how a threat operates is crucial in developing effective countermeasures.
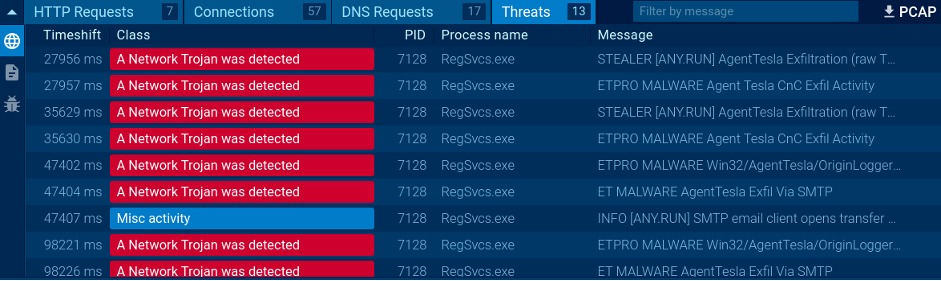
The ANY.RUN sandbox detects all network threats using Suricata IDS
ANY.RUN’s sandbox provides comprehensive, in-depth analysis of threats’ network activity, registry and system changes, as well as processes.

Users can view the processes launched during analysis as a graph
This information can be used to understand the threat’s behavior, its target, and the potential damage it can cause.
Threat Reporting
Another critical aspect of a malware sandbox is its reporting functionality. After the analysis of a suspicious file or URL, the sandbox generates a comprehensive report detailing its findings. This report is a crucial tool for cybersecurity professionals, providing them with the information they need to make informed decisions about potential threats.
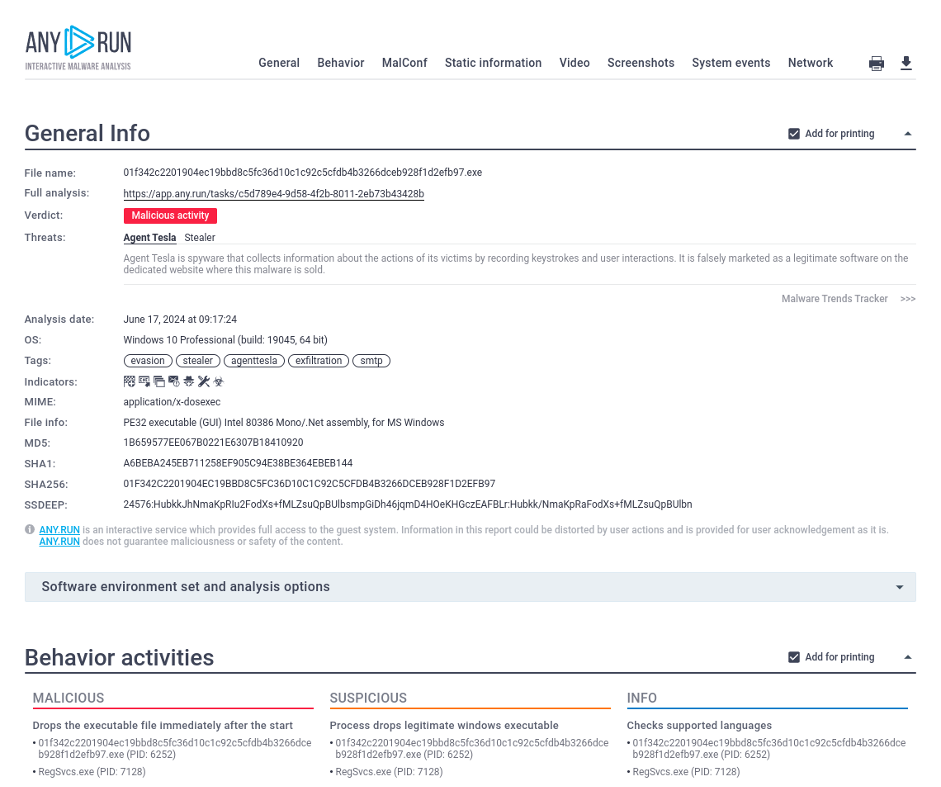
Threat report provided by ANY.RUN
Above you see an example of a sandbox report that can be downloaded and shared.
Training and Education
Malware sandboxes also double as efficient training resources. ANY.RUN’s collaborative platform for teams is perfect for offering hands-on learning experiences to junior analysts, while enabling senior specialists to easily track performance. This approach can significantly enhance an organization’s overall cybersecurity awareness and readiness.
Conclusion
Incorporating a malware sandbox like ANY.RUN into your cybersecurity strategy can significantly enhance your threat detection and response capabilities. By providing a safe, isolated environment for threat analysis, these tools offer a proactive approach to cybersecurity.
You can request a 14-day trial of ANY.RUN to try all advanced sandbox features for free!
Lynn Martelli is an editor at Readability. She received her MFA in Creative Writing from Antioch University and has worked as an editor for over 10 years. Lynn has edited a wide variety of books, including fiction, non-fiction, memoirs, and more. In her free time, Lynn enjoys reading, writing, and spending time with her family and friends.















